| CPC H04L 63/145 (2013.01) [G06N 20/00 (2019.01); H04L 43/12 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/1466 (2013.01); H04L 63/1491 (2013.01); H04L 63/20 (2013.01); H04L 41/22 (2013.01)] | 18 Claims |
|
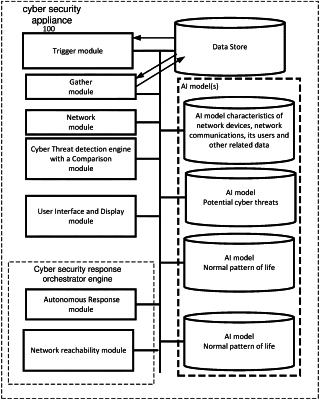
1. An apparatus, comprising:
a network reachability module configured to cooperate with a cyber-security response-orchestrator engine configured to mitigate a detected cyber threat,
where the network reachability module is configured to map and dynamically track network reachability of the cyber-security response-orchestrator engine, where the network reachability module has a tracking module to 1) monitor network traffic and 2) keep track of known devices and/or known subnets on a network, which is updated as previously unknown devices and subnets on the network are detected, and
where the network reachability module has a trigger module configured to cooperate with the tracking module, where the trigger module and the tracking module are further configured to cooperate to repeatedly, on their own initiative, go through and check network addresses to see when at least one network device in each known subnet can be reached, via at least one of a generated spoofed transmission and response communication, and then periodically recheck the network addresses with network devices in each known subnet over time in order to determine whether the known devices and/or known subnets on the network currently either 1) can receive or 2) cannot receive protocol communications from a location of a host device for the cyber-security response-orchestrator engine.
|