| CPC H04L 63/1433 (2013.01) [H04L 43/045 (2013.01); H04L 63/1416 (2013.01)] | 20 Claims |
|
1. A system comprising:
computer-readable memory storing computer-executable instructions; and
one or more hardware processors in communication with the computer-readable memory and programmed by the computer-executable instructions;
wherein the system is configured to at least:
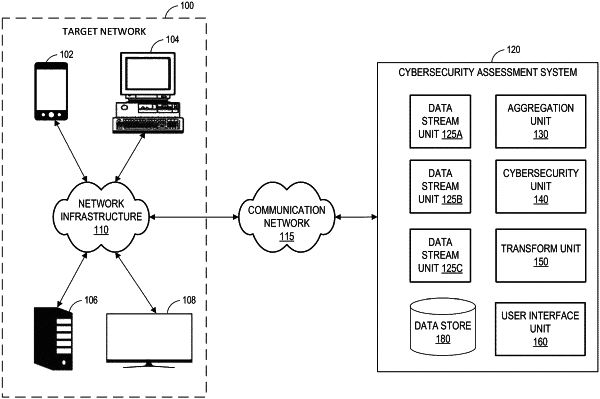
generate a plurality of data streams based at least partly on scanning a target network, wherein a first data stream of the plurality of data streams comprises data representing characteristics of devices on the target network, wherein a second data stream of the plurality of data streams comprises data representing events detected on the target network, and wherein a third data stream of the plurality of data streams comprises data representing vulnerabilities associated with devices on the target network;
generate processed scan data based at least partly on the plurality of data streams;
generate vulnerability data based on the processed scan data, wherein the vulnerability data comprises data regarding a plurality of vulnerabilities, and wherein each vulnerability of the plurality of vulnerabilities is represented by at least a vulnerability identifier and a severity label corresponding to a severity level of a severity hierarchy;
present a first graph comprising at least a first selectable segment visually representing a first quantity of vulnerabilities associated with a first severity label, and a second selectable segment visually representing a second quantity of vulnerabilities associated with a second severity label;
identify a cybersecurity assessment framework against which the target network is to be assessed;
determine an initial score for one or more cybersecurity factors associated with the cybersecurity assessment framework;
determine an adjustment for one or more of the determined initial scores based at least partly on the processed scan data, wherein a first adjustment to a first initial score is determined by applying a set of rules, associated with a first cybersecurity factor, to a subset of the processed scan data;
generate an overall cybersecurity score based at least partly on applying the determined adjustments to the determined initial scores;
present a visual representation of the overall cybersecurity score;
identify a plurality of events using the plurality of data streams, wherein individual events are associated with a threshold level of severity; and
present a visual representation of the plurality of events.
|