| CPC H04L 63/1416 (2013.01) [H04L 41/22 (2013.01); H04L 51/08 (2013.01); H04L 51/212 (2022.05); H04L 63/1425 (2013.01); H04L 63/1466 (2013.01)] | 20 Claims |
|
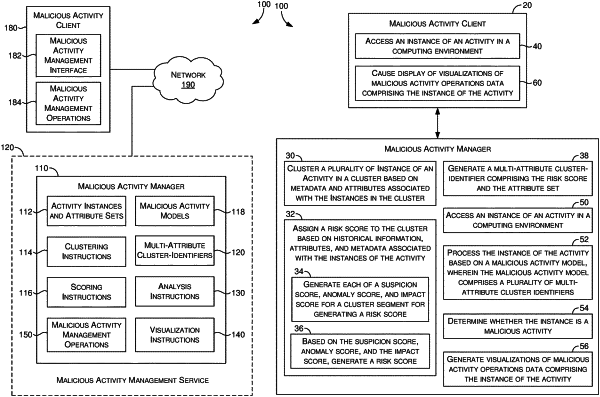
1. A computer-implemented method, the method comprising:
accessing an instance of an activity in a computing environment, wherein the instance of the activity comprises an attribute set of the instance, wherein attribute set of the instance comprises at least one attribute;
receiving the instance of the activity at a malicious activity model that comprises a multi-attribute cluster identifier associated with a previous instance of the activity, the multi-attribute cluster-identifier comprising a risk score and an attribute set of the multi-attribute cluster-identifier, wherein the attribute set of the multi-attribute cluster-identifier comprises at least one attribute, the risk score and the attribute set of the multi-attribute cluster-identifier indicate a likelihood that the instance of the activity is a malicious activity,
wherein the risk score is based on the following: a suspicion score, an anomaly score, and an impact score, each based on information from a cluster that is indicative of malicious activity,
wherein the suspicion score is based on information about a tenant of the computing environment,
wherein the anomaly score is based on information regarding a sender,
wherein the impact score is based on a position of one or more individuals targeted by an instance of the activity in a corresponding cluster,
wherein the multi-attribute cluster-identifier is based on the suspicion score, the anomaly score, the impact score, and the risk score, wherein the suspicion score, the anomaly score, and the impact score are associated with a cluster segment having a type of activity, wherein the type of activity is associated with an attribute set of the type of activity,
determining, using the malicious activity model, that the instance of the activity is a malicious activity based on comparing the attribute set of the instance of the activity to the attribute set of the multi-attribute cluster-identifier, wherein the attribute set of the instance of the activity matches the attribute set of the multi-attribute cluster-identifier, the risk score and the attribute set of the multi-attribute cluster-identifier indicate a likelihood that the instance of the activity is a malicious activity;
generating a visualization of malicious activity operations data comprising the instance of the activity, wherein the visualization identifies the instance of the activity as the malicious activity.
|