| CPC H04L 63/14 (2013.01) [G06F 21/566 (2013.01); G06F 21/577 (2013.01); H04L 63/102 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/205 (2013.01); H04L 67/306 (2013.01); G06F 2221/034 (2013.01)] | 18 Claims |
|
1. A computer-implementable method for performing a security operation, comprising:
monitoring a plurality of electronically-observable actions of a first entity, the plurality of electronically-observable actions of the first entity corresponding to a respective first plurality of events enacted by the first entity, the first entity comprising a first user entity;
monitoring a plurality of electronically-observable actions of a second entity, the plurality of electronically-observable actions of the second entity corresponding to a respective second plurality of events enacted by the second entity, the second entity comprising a second user entity;
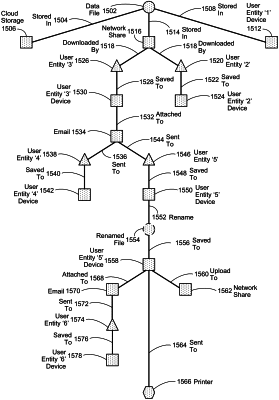
determining whether a first event of the respective first plurality of events and a second event of the respective second plurality of events comprise an entity interaction between the first entity and the second entity, the entity interaction between the first entity and the second entity comprises a conveyance of data;
generating an entity interaction map, the entity interaction map providing a representation of the entity interaction between the first entity and the second entity, the entity interaction map providing a historical mapping of the conveyance of data between the first entity to the second entity, the generating the entity interaction map including generating a representation of a concatenation of correlated entity interactions;
performing a security analytics operation via a security analytics system using the entity interaction map, the security analytics system executing on a hardware processor, the security analytics operation detecting an anomalous event associated with the entity interaction between the first entity and the second entity, the anomalous event being related to the conveyance of data between the first entity to the second entity; and,
using the entity interaction map to perform a forensics analysis upon detection of the anomalous event.
|