| CPC H04L 63/04 (2013.01) [G06F 21/566 (2013.01); G06F 21/577 (2013.01); H04L 63/102 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/205 (2013.01); H04L 67/306 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
1. A computer-implementable method for performing a security operation, comprising:
monitoring an entity, the monitoring observing at least one electronically-observable data source;
identifying a security related activity of the entity, the security related activity being of analytic utility;
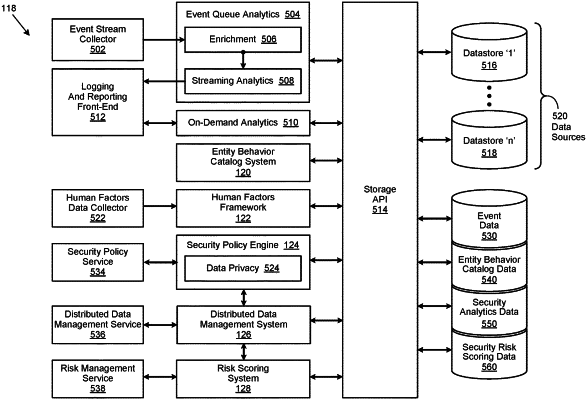
accessing an entity behavior catalog based upon the security related activity, the entity behavior catalog storing entity behavior catalog data, the entity behavior catalog data comprising an inventory of entity behaviors and a human-centric risk modeling framework, the human-centric risk modeling framework enabling quantification of a human-centric factor associated with the entity, the human-centric factor comprising a motivation factor, a stressor factor and an organizational dynamics stressor factor, the human-centric factor having an associated effect on the entity, the motivation factor representing a user entity behavior that provides an indication of a motivation for enacting the user entity behavior, the stressor factor representing an issue influencing the user entity behavior, the organizational stressor factor representing an event occurring within an organization affecting the user entity behavior; and
performing a security operation via a distributed security analytics environment, the security operation being performed by at least one of an entity edge component and a security analytics system, the entity edge component executing the security operation on a hardware processor associated with the entity edge component, the security analytics system executing the security operation on a hardware processor associated with the security analytics system, the security operation using the entity behavior catalog data stored within the entity behavior catalog based upon the security related activity.
|