| CPC H04L 63/102 (2013.01) [H04L 41/22 (2013.01); H04L 63/105 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
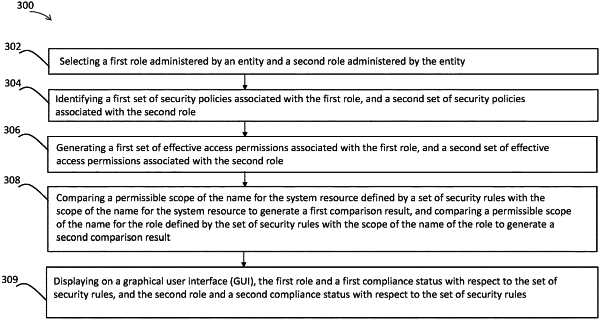
1. A computer-implemented method for determining compliance to security rules, the method comprising:
selecting a first role administered by an entity and a second role administered by the entity;
identifying a first set of security policies associated with the first role, and a second set of security policies associated with the second role, wherein the first set of security policies includes a first security policy and a second security policy;
generating a first set of effective access permissions associated with the first role, and a second set of effective access permissions associated with the second role, wherein the first set of effective access permissions is generated based on the first set of security policies by resolving at least a conflict between the first security policy and the second security policy, and wherein the first set of effective access permissions defines a scope of a name for a system resource, or defines a scope of a name for a role;
comparing a permissible scope of the name for the system resource defined by a set of security rules with the scope of the name for the system resource to generate a first comparison result, and comparing a permissible scope of the name for the role defined by the set of security rules with the scope of the name of the role to generate a second comparison result; and
displaying on a graphical user interface (GUI), the first role and a first compliance status with respect to the set of security rules, and the second role and a second compliance status with respect to the set of security rules, wherein the first compliance status of the first role with respect to the set of security rules is determined based on the first comparison result and the second comparison result.
|