| CPC H04L 63/083 (2013.01) [H04L 9/0643 (2013.01); H04L 9/3226 (2013.01); H04L 9/3271 (2013.01); H04L 63/0869 (2013.01); H04L 63/10 (2013.01); H04W 12/069 (2021.01); H04W 12/084 (2021.01)] | 20 Claims |
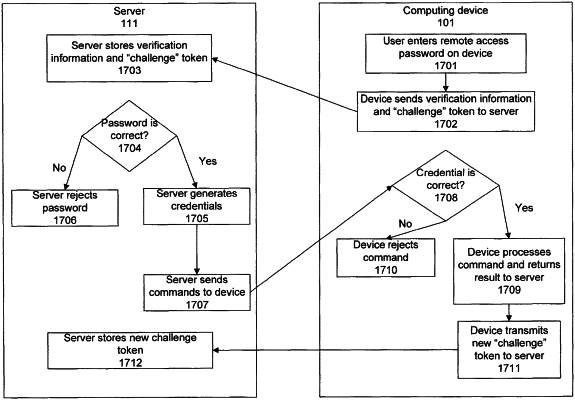
|
1. A computer program product comprising computer-readable program code to be executed by one or more processors when retrieved from a non-transitory computer-readable medium, the program code including instructions to:
receive a notification regarding a computing device;
send at least one instruction, in response to the notification, to deny use of at least one computing device function until the computing device receives at least one instruction to permit the use of the at least one denied computing device function;
receive a request from a requesting party to initiate an action on the computing device, the action requiring the use of the at least one denied computing device function;
send, in response to the request, a message to a set of designated authorizing parties, the message regarding whether to permit the use of the at least one denied computing device function;
authenticate a first party, the first party being from the set of designated authorizing parties;
authenticate a second party, the second party being from the set of designated authorizing parties, the second party being different from the first party;
receive authorization from the first party;
receive authorization from the second party; and
after successful authentications of the first and second parties and receipt of the authorization from the first party and receipt of the authorization from the second party, send at least one instruction to the computing device that permits the use of the at least one denied computing device function and permits the action requiring the use of the at least one denied computing device function.
|