| CPC H04L 41/0894 (2022.05) [H04L 41/0893 (2013.01); H04L 63/20 (2013.01)] | 17 Claims |
|
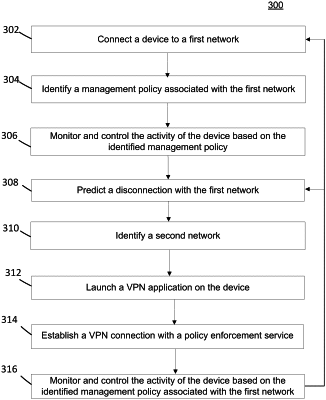
1. A method comprising:
connecting, by a device, to a first network provided a service provider;
identifying, by the device, a profile for a user, the user profile corresponding to the first network, the user profile comprising a management policy associated with the first network that is implemented upon the connection to the first network, the management policy comprising executable instructions related to read/write access by the device to a network resource, the management policy being managed by a policy management service provided by a cloud system;
analyzing, by the device, the management policy associated with the first network;
determining, by the device, based on the analysis of the management policy, a set of network configurations for the user, the set of network configurations comprising specific read/write controls for the user;
controlling, by the device based on the implemented management policy and the determined set of network configurations, activity by the device on the first network;
determining, by the device, to switch to a second network;
executing, by the device, a virtual private network (VPN) application, the execution of the VPN application causing establishment of a VPN connection with the policy management service via the second network, wherein the VPN application enables the management policy of the first network to be applied to network activity by the device on the second network; and
controlling, by the device, via the VPN application, the network activity of the device on the second network based on the read/write access of the management policy and the determined set of network configurations.
|