| CPC G07C 9/00563 (2013.01) [G06V 40/10 (2022.01); G06V 40/20 (2022.01); G08B 21/18 (2013.01); G10L 17/24 (2013.01)] | 16 Claims |
|
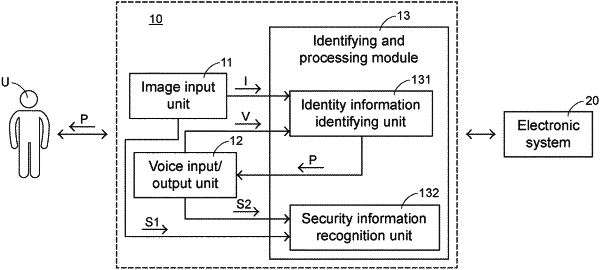
1. A security authentication method, at least comprising steps of:
(a) inputting a to-be-recognized image information and a to-be-recognized voice information about a user;
(b) identifying and judging whether the to-be-recognized image information and the to-be-recognized voice information comply with a registered image information and a registered voice information, respectively;
(c) if the to-be-recognized image information and the to-be-recognized voice information comply with the registered image information and the registered voice information, respectively, generating and outputting a security information prompt signal;
(d) providing a to-be-recognized security information by the user in response to the security information prompt signal;
(e) identifying and judging whether the to-be-recognized security information complies with an abnormal warning information, wherein the abnormal state at least comprises: a voice string representing that the user is in at least one of a physical discomfort state and a hostage state, or a gesture action representing that the user is in at least one of the physical discomfort state and the hostage state; and
(f) if the to-be-recognized security information complies with the abnormal warning information, performing an abnormal state warning and processing process,
wherein when the abnormal state warning and processing process is performed in the step (f), at least one of a door locking action and a system disabling action is performed.
|