| CPC G06Q 40/04 (2013.01) [G06F 16/182 (2019.01); G06N 3/08 (2013.01); G06N 5/02 (2013.01); G06Q 10/10 (2013.01); G06Q 10/20 (2013.01); G06Q 20/381 (2013.01); G06Q 20/389 (2013.01); G06Q 20/3829 (2013.01); G06Q 20/40145 (2013.01); G06Q 50/182 (2013.01); H04L 9/3231 (2013.01); H04L 63/0435 (2013.01); H04L 63/126 (2013.01); G06F 21/602 (2013.01); G06Q 50/205 (2013.01); G06Q 2230/00 (2013.01); H04L 63/0272 (2013.01)] | 20 Claims |
|
1. A computer implemented method for a secure communication environment configured to manage a decentralized venture capital (“VC”) fund in a decentralized autonomous organization (“DAO”), said method comprising:
receiving, in the secure communication environment, a plurality of information about a collateral that underwrites a first number of stable coins where the stable coins are funding for said decentralized venture capital fund;
receiving, in the secure communication environment, a request for an investment from a company;
receiving, in the secure communication environment, from a plurality of shareholders of said decentralized venture capital fund, a first plurality of votes based on said request;
approving said request automatically, in the secure communication environment, when a first number of approval votes, based on said first plurality of votes, exceeds a predetermined investment threshold;
transferring, in the secure communication environment, to said company, a second number of stable coins from said first number of stable coins as the investment based on the approval;
transferring, in the secure communication environment, at least one stable coin, from said second number of stable coins, to a seller as payment for at least one of a good and service; and
converting, in the secure communication environment, said at least one stable coin into at least one share option in said decentralized venture capital fund,
where the secure communication environment is generated by downloading a CCS application, from a central control system (CCS), which includes at least one processor and memory configured to store computer program code instructions, to the computers of users of the decentralized autonomous organization, the CCS application generating secure authentication messages between the users and the CCS, the secure authentication messages implementing authentication with encryption that perform the steps of:
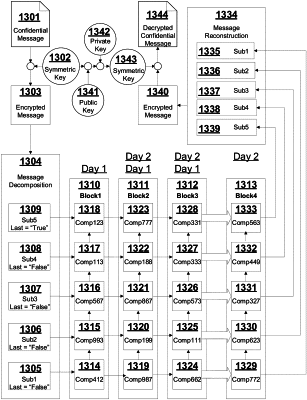
storing securely, on a sender's computer, a plurality of authentication and authorization information, based on using at least one of a cryptographic public encryption key and a cryptographic symmetric encryption key in a process that encrypts a secure authentication message;
decomposing, by the CCS application running on the sender's computer, an encrypted version of said secure authentication message into a block of linked and ordered subcomponents that are stored randomly across a first plurality of member computers that are selected from a predetermined list of participating computers, a final subcomponent in the link of subcomponents flagged as a last subcomponent;
randomly selecting, by the CSS application running on the sender's computer, three member computers on which to copy a first subcomponent of the secure authentication message;
randomly selecting, by each of the three computers which have a copy of the first subcomponent of the secure authentication message, a member computer for which to copy a second subcomponent of the secure authentication message, and repeating the process of randomly selecting a member computer to copy the next ordered subcomponent of the secure authentication message by the computer that copied the ordered subcomponent that immediately precedes the next ordered subcomponent, until the final subcomponent of the block which is flagged as the last subcomponent has been copied, which generates three copies of blocks of linked and ordered subcomponents of the secure authentication message, where each computer which stores a copy of a subcomponent knows only of the computer which was randomly selected by that computer;
using a unique, configurable authorization identifier as a file name for each individual subcomponent, in said link of subcomponents, on each member computer that stores a subcomponent;
periodically, by the computer storing a newest copy of the first subcomponent of the secure authentication message, randomly selecting a member computer for which to copy the first subcomponent of the secure authentication message and generating a new block of linked and ordered subcomponents of the secure authentication message;
deleting an oldest block of linked and ordered subcomponents of the secure authentication message after generating the new block of linked and ordered subcomponents of the secure authentication message;
recombining, on a receiver's computer, the encrypted version of the secure authentication message from the new block of linked and ordered subcomponents of the secure authentication message after verifying, by the receiver's computer, the unique, configurable authorization identifier transmitted by the sender's computer; and
recovering said secure authentication message, based on using at least one of a cryptographic private encryption key and said cryptographic symmetric encryption key in a process that decrypts said encrypted version of said secure authentication message, where said cryptographic private encryption key matches said cryptographic public encryption key.
|