| CPC G06Q 30/0185 (2013.01) [G06F 16/29 (2019.01); G06F 16/587 (2019.01); G06Q 20/1085 (2013.01); G06Q 20/407 (2013.01); G06Q 30/0205 (2013.01); G06Q 40/12 (2013.12); G06V 20/10 (2022.01); G06V 40/172 (2022.01)] | 18 Claims |
|
1. A computer-implemented method for location-based anomaly detection based on geotagged digital photographs, at least a portion of the method being performed by a computer comprising one or more processors, the method comprising:
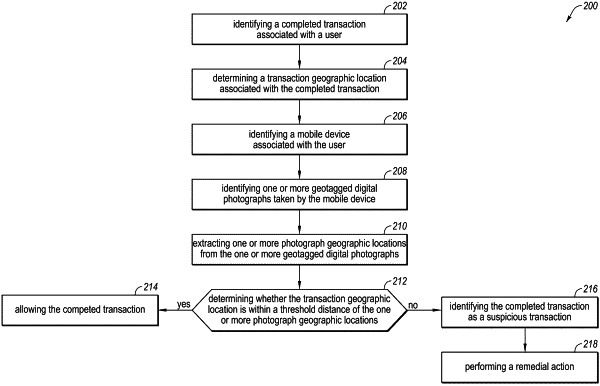
identifying, by a processor, a completed transaction associated with a user, wherein the completed transaction is a financial transaction between the user and a third party;
determining, by the processor, a transaction geographic location and a transaction time period associated with the completed transaction;
identifying, by the processor, a mobile device associated with the user;
identifying, by the processor, one or more geotagged digital photographs taken by the mobile device, wherein the mobile device includes a global positioning system (GPS) receiver that identifies photograph geographic locations for each of the one or more geotagged digital photographs;
extracting, by the processor, the photograph geographic locations from each of the one or more geotagged digital photographs and determining threshold distances from each of the photograph geographic locations;
determining, by the processor, that the transaction geographic location is not within a threshold distance of the photograph geographic locations of the one or more geotagged digital photographs; and
performing a remedial action, wherein performing the remedial action includes:
presenting an alert on the mobile device informing the user of a suspicious transaction,
presenting an option on the mobile device for the user to undo the suspicious transaction, or
marking the completed transaction as being suspicious on a display of the mobile device.
|