| CPC G06F 9/4406 (2013.01) [G06F 21/606 (2013.01); H04W 24/04 (2013.01)] | 18 Claims |
|
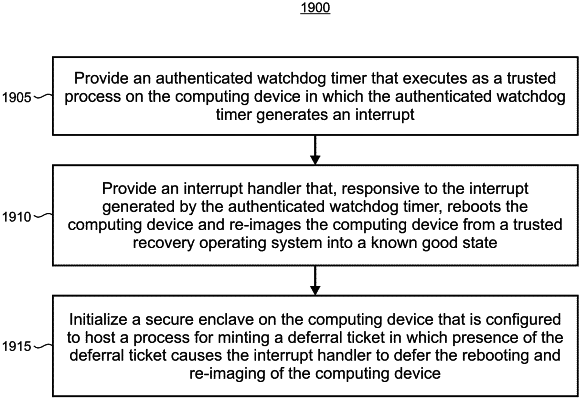
10. A computing device, comprising:
at least one processor that supports a secure execution environment;
at least one security monitor configured for runtime introspection of a runtime state of the computing device;
hardware-protected System Management Random Access Memory (SMRAM) that is configured for use by the at least one processor to store code associated with a System Management Mode (SMM);
at least one non-transitory computer-readable storage device storing computer-executable instructions thereon and further storing code for an operating system (OS) thereon; and
an isolated read-only partition of the at least one non-transitory computer-readable storage device storing a recovery OS thereon,
wherein the instructions, when executed by the least one processor, cause the computing device to
execute a trusted Unified Extensible Firmware Interface (UEFI) providing a runtime that executes System Management Mode (SMM) code;
execute the SMM code to instantiate a System Management Interrupt (SMI) handler that executes on the computing device to cause the computing device to reboot and be re-imaged from a trusted recovery operating system (OS);
initialize a UEFI enclave in the UEFI runtime as a pre-boot process on the computing device;
configure an untrusted OS to initialize a deferral ticket minting enclave as a post-boot process on the computing device, in which the UEFI enclave and the deferral ticket minting enclave share a common enclave author, and in which the deferral ticket minting enclave is configured for minting a deferral ticket, wherein presence of the deferral ticket causes the SMI handler to defer the reboot and re-imaging of the computing device; and
utilize an enclave versioning support protocol by which enclaves having a common author are each enabled to provision a common symmetric key to provide cryptographic security for the deferral ticket.
|