| CPC G06F 21/62 (2013.01) [G06F 21/602 (2013.01); G06V 20/41 (2022.01); G06V 20/52 (2022.01); H04N 7/183 (2013.01); G06F 2221/2111 (2013.01); G06V 20/44 (2022.01)] | 33 Claims |
|
1. A method for limiting video surveillance to authorized uses, comprising:
at a surveillance system:
receiving a video footage of an area under surveillance from a security camera;
analyzing the video footage to detect a plurality of events in the video footage;
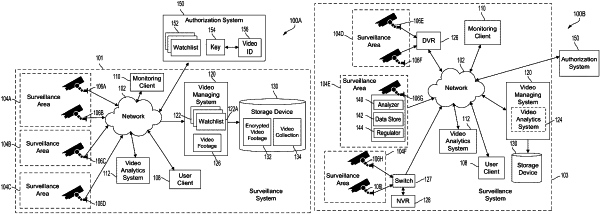
generating a video collection comprising a copy of a plurality of portions of the video footage based on applying a watchlist indicating an approved event of interest to the analyzed video footage, wherein each copied portion is detected to include the approved event;
encrypting the video footage using a first key to restrict a first user from accessing other portions of the video footage that do not include the approved event; and
providing the first user access to the video collection;
wherein the watchlist comprises an indication of the approved event and a plurality of associated parameters for video surveillance, the plurality of parameters including a location approved for surveilling the event, and the method comprises:
determining which video segments of the video footage meets the plurality of parameters and includes the approved event, wherein the plurality of copied portions of the video footage comprises the determined video segments, and
determining that the video footage is associated with the approved location before generating the video collection, wherein determining that the video footage is associated with the approved location comprises analyzing the video footage to identify one or more features that uniquely identifies the location or determining that metadata of the received video footage indicates the location, and
wherein the method comprises:
transmitting the first key to an authorization system that controls access to a plurality of encrypted video footages,
receiving a notification from the authorization system indicating that the first key was received and securely stored by the authorization system, and
irrecoverably deleting the first key from the surveillance system.
|