| CPC G06F 21/577 (2013.01) [G06F 21/44 (2013.01); G06F 21/52 (2013.01); G06F 21/552 (2013.01); G06F 21/56 (2013.01); G06F 2221/033 (2013.01)] | 19 Claims |
|
1. A method of detecting an exploit of a vulnerability of a computing device, the method comprising:
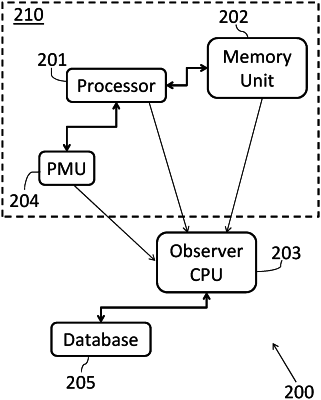
receiving an execution flow of at least one process running in a first physical processor of the computing device, wherein the execution flow is received from a performance monitoring unit (PMU) of the first physical processor;
receiving memory pages from a memory of the computing device;
continuously checking, by another physical processor which is physically separate from the first processor, the execution flow of the first processor, to identify a memory value that is mapped to stack memory by the another physical processor;
reconstructing the execution flow of the process on the another physical processor based on the execution flow received from the PMU and the memory pages;
running at least one exploit detection algorithm on the reconstructed execution flow of the process in order to identify an exploit attempt; and
issuing an alert.
|