| CPC H04L 9/3247 (2013.01) [H04L 47/762 (2013.01); H04L 47/827 (2013.01); H04L 47/828 (2013.01)] | 24 Claims |
|
1. A method comprising:
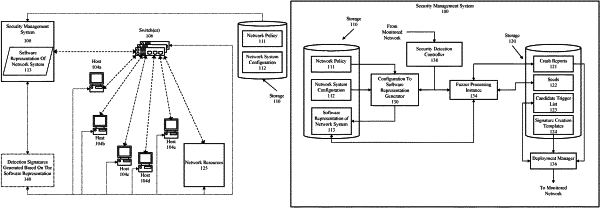
identifying a plurality of candidate triggers selected for implementation as detection signatures, wherein the plurality of candidate triggers correspond to state-to-state transitions identified by analyzing a software representation of a computer network, the software representation represents actions that can be taken on the computer network, and the software representation of the computer network was generated based on network configuration data and network policy data that specify access rights; and
processing one or more candidate triggers of the plurality of candidate triggers to generate detection signature instances, wherein each of the one or more candidate triggers are processed by:
selecting a respective candidate trigger of the one or more candidate triggers;
identifying a corresponding detection signature template;
duplicating the corresponding detection signature template; and
modifying the duplicate detection signature template to form a respective detection signature.
|