| CPC H04L 63/20 (2013.01) [H04L 63/101 (2013.01)] | 13 Claims |
|
1. A method implemented in a security control platform to enforce scope-based security controls, comprising:
providing a cloud intelligence data model that, for a particular enterprise, associates resources, activities and associated permissions associated with multiple cloud providers and accounts;
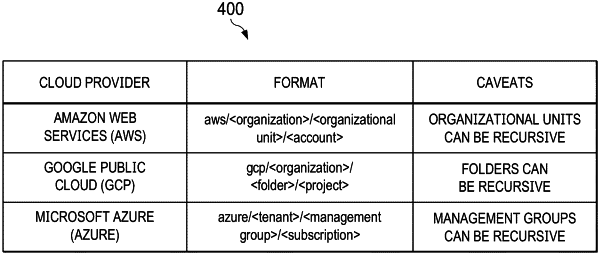
with respect to a given cloud provider of the multiple cloud providers used by the particular enterprise, identifying a scope, wherein the scope is any point within a delimited path into a particular cloud environment of that given cloud provider, wherein the given cloud provider and at least one other cloud provider of the multiple cloud providers define contents of a respective scope differently from one another;
normalize the identified scope for use by the security control platform to optimally apply a security control;
based at least in part on the cloud intelligence data model, configuring a security policy for the particular cloud environment of the given cloud provider, the security policy by default denying all permissions with respect to the identified scope;
instantiating the security policy in the particular cloud environment of the given cloud provider of the multiple cloud providers used by the particular enterprise; and
using the instantiated security policy, and with respect to the identified scope associated with the given cloud provider, implementing permissions-on-demand with respect to one or more identities within the particular cloud environment.
|