| CPC H04L 63/0263 (2013.01) [G05B 19/05 (2013.01); G06Q 10/0875 (2013.01); H04L 12/4641 (2013.01); H04L 41/0803 (2013.01); H04L 41/0893 (2013.01); H04L 43/026 (2013.01); H04L 47/20 (2013.01); H04L 47/2441 (2013.01); H04L 47/323 (2013.01); H04L 63/20 (2013.01)] | 17 Claims |
|
1. A method comprising:
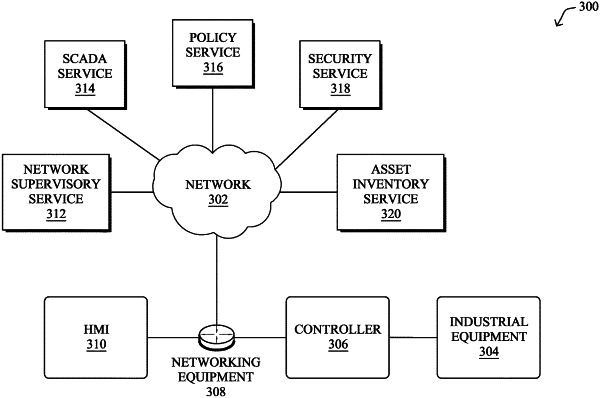
receiving, at a networking device in a network, a policy for an endpoint device in the network, the policy specifying one or more component tags and one or more activity tags that were assigned to the endpoint device based on deep packet inspection of traffic associated with the endpoint device, wherein the one or more component tags that were assigned to the endpoint device are indicative of at least one of: a device type of the endpoint device or software executed by the endpoint device;
identifying, by the networking device, a set of tags for a particular traffic flow in the network associated with the endpoint device based on receiving, from a telemetry exporter in the network, a traffic flow record for the particular traffic flow, wherein the set of tags are embedded in the traffic flow record, and wherein the set of tags comprises one or more component tags or activity tags associated with the particular traffic flow;
making, by the networking device, a determination that the particular traffic flow violates the policy based on the set of tags for the particular traffic flow comprising a tag that is not in the policy, wherein the determination that the particular traffic flow violates the policy is made by comparing the set of tags for the particular traffic flow with the one or more component tags and the one or more activity tags specified by the policy; and
initiating, by the networking device and based on the determination that the particular traffic flow violates the policy, a corrective measure with respect to the particular traffic flow.
|