| CPC H04L 9/0891 (2013.01) [H04L 63/029 (2013.01); H04L 63/164 (2013.01)] | 30 Claims |
|
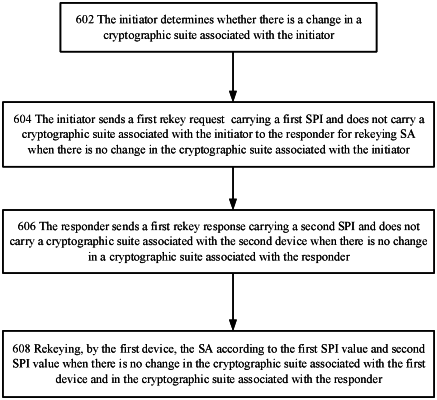
1. A method for rekeying a security association (SA) applied in a network system including a first network device and a second network device, wherein an Internet Key Exchange (IKE) tunnel and an Internet Protocol Security (IPSec) tunnel are established between the first network device and the second network device, the method comprising:
determining, by the first network device, whether there is a change in a cryptographic suite associated with the first network device;
sending, by the first network device, a first rekey request to the second network device for rekeying the SA when there is no change in the cryptographic suite associated with the first network device, wherein the first rekey request carries a first Security Parameter Index (SPI) and does not carry the cryptographic suite associated with the first network device;
receiving, by the first network device, a first rekey response from the second network device, wherein the first rekey response carries a second SPI and does not carry a cryptographic suite associated with the second network device when there is no change in the cryptographic suite associated with the second network device;
rekeying, by the first network device, the SA according to the first SPI and the second SPI when there is no change in the cryptographic suite associated with the first network device and there is no change in the cryptographic suite associated with the second network device.
|