| CPC H04L 63/20 (2013.01) [H04L 45/38 (2013.01); H04L 47/20 (2013.01); H04L 49/70 (2013.01); H04L 63/0263 (2013.01); H04L 63/0272 (2013.01); H04L 67/12 (2013.01)] | 24 Claims |
|
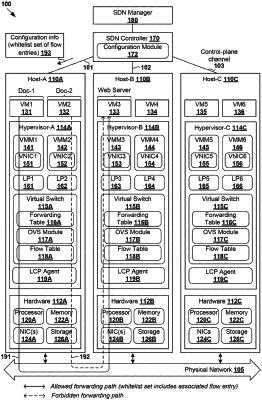
1. A method for a network manager to perform flow-based forwarding element configuration in a network environment that includes the network manager, a flow-based forwarding element, and a group of workloads, the method comprising:
obtaining a set of security policies associated with the group of workloads, wherein the set of security policies allows communication between a destination and a first workload from the group, but blocks communication between the destination and a second workload from the group;
based on the set of security policies, identifying an allowed forwarding path between the destination and the first workload;
configuring a whitelist set of flow entries that:
includes a first flow entry that specifies match fields and a first action to allow communication over the allowed forwarding path, but
excludes flow entries, associated with actions to block communications between the destination and the workloads, such that a second flow entry, which specifies a second action to block communication over a forbidden forwarding path between the destination and the second workload, is absent in the whitelist set and so communication between the destination and the second workload is automatically blocked due to the second flow entry being absent in the whitelist set,
wherein the flow entries included in the whitelist set are non-hierarchical and are configured based on the set of security policies prior to packet detection, and wherein the match fields include transport layer information and network layer information; and
sending configuration information to the flow-based forwarding element to cause the flow-based forwarding element to apply the whitelist set to:
in response to detecting a first packet that is addressed from the first workload to the destination and that matches with the match fields specified by the first flow entry, perform the first action to forward the first packet to the destination; and
in response to detecting a second packet that is addressed from the second workload to the destination and that does not match with any flow entry in the whitelist set, drop the second packet.
|