| CPC H04L 63/166 (2013.01) [H04L 61/5014 (2022.05); H04L 63/0869 (2013.01); H04L 63/0884 (2013.01)] | 20 Claims |
|
1. A non-transitory computer-readable medium storing instructions that, when executed, cause one or more processors to perform operations, comprising:
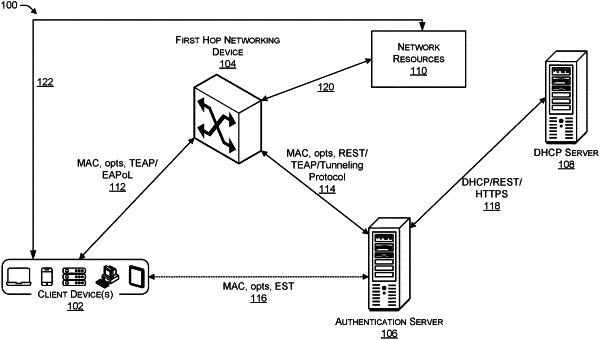
at an authentication server, receiving, from a client device, a request for a first dynamic host configuration protocol (DHCP) option;
determining if the authentication server implements DHCP;
based at least in part on a determination that the authentication server does not implement a DHCP, transmitting an application program interface (API) call to a DHCP server associated with the authentication server acting as a DHCP gateway, a representational state transfer (REST) wrapper being applied to the API call such that the first DHCP option is secured;
receiving a response from the DHCP server; and based at least in part on the authentication server does implement DHCP protocol, transmitting to the client device a response from the authentication server; transmitting the response received from the DHCP server to the client device, wherein the response received from the DHCP server comprises: the first DHCP option; and a second DHCP option separated from the first DHCP option, the second DHCP option being a non-requested option with respect to the first DHCP option and comprising a pointer to the authentication server.
|