| CPC H04L 63/1433 (2013.01) [H04L 63/20 (2013.01)] | 18 Claims |
|
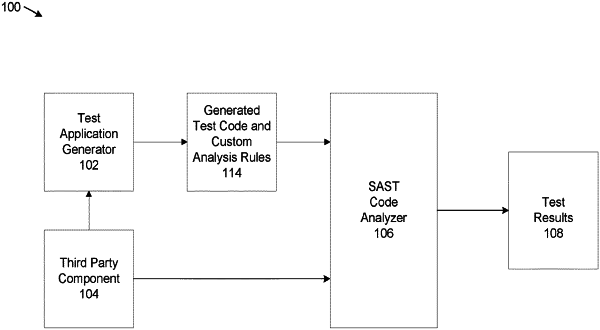
1. A method for identifying security vulnerabilities in a software library, the method comprising:
generating a test application for the software library;
identifying methods and functions used in the software library;
using the test application to implement a method call or a function call for each identified method and function, respectively, in the software library;
analyzing the test application and the software library in a static application security testing (SAST) code analyzer, the analyzing of the test application and the software library in the SAST code analyzer comprising identifying a plurality of software entry points in the software library;
obtaining one or more test results from the SAST code analyzer, wherein the one or more test results include manual test results in which one or more individuals have identified false positives;
using the manual test results to identify security vulnerabilities in the software library; and
using one of the manual test results to generate custom rules used when testing new applications that use the software library, wherein the custom rules are automatically generated by a custom rules generator, and wherein the custom rules model a behavior of a third party component and include passing tainted data from the test application to the software library.
|