| CPC H04L 63/1433 (2013.01) [H04L 63/1425 (2013.01); H04L 41/069 (2013.01); H04L 43/062 (2013.01)] | 20 Claims |
|
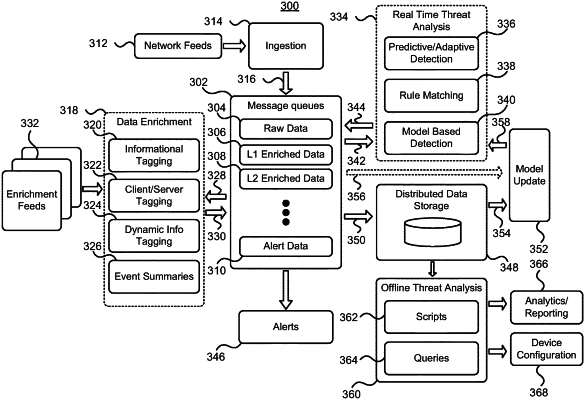
1. A cyber-threat intelligence (CTI) infrastructure comprising:
a plurality of network devices each collecting network reporting information;
a collection of at least one CTI server, the collection configured for:
receiving the network reporting information collected by the plurality of network devices, the network reporting information comprising a plurality of records each comprising an indication of a source and destination of network traffic;
storing the received plurality of records in a raw record message queue;
enriching the network reporting information with enrichment data by adding one or more tags of enrichment data to records of the network reporting information comprising, for each of the records of the network reporting information:
identifying each of a source and a destination of the respective record retrieved from the message queue as a client or a server based at least in part on a portion of the network reporting information comprising one or more a source IP address, a destination IP address, a source port number, and a destination port number;
tagging the respective record by adding an indication of whether the source and destination is identified as the client or server; and
storing the enhanced record with the tagged client or server in an enhanced record message queue;
processing, by one or more real time threat analysis components, the plurality of records in the raw record message queue and the enriched network reporting information of enhanced records stored in the enhanced record message queue comprising the plurality of records with respective sources and destinations tagged as either clients or servers to identify the potential security vulnerabilities;
wherein each of the one or more real time threat analysis components comprises a model based detection component and one or more of: a predictive detection component, an adaptive detection component, and a rule matching component;
storing, in a storage component, the enriched network reporting information;
processing by an offline threat analysis component the stored enriched network reporting information to further identify the potential security vulnerabilities;
updating the one or more real time and/or offline threat analysis components used to process the enriched network reporting information using the enriched network reporting information;
providing the identified potential security vulnerabilities to an alert component;
transmitting from the alert component one or more alerts based on at least one identified potential security vulnerabilities;
processing the enriched network reporting information by running one or more scripts or queries against the enriched network reporting information; and
configuring one or more network devices comprising at least one of a firewall and a router based on the results of the one or more scripts or queries.
|