| CPC H04L 63/1425 (2013.01) [H04L 63/145 (2013.01); H04L 61/4511 (2022.05)] | 20 Claims |
|
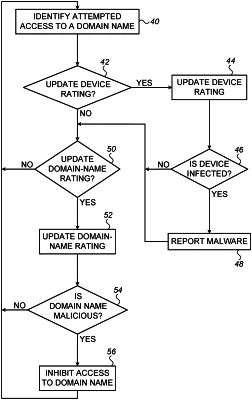
1. A method for monitoring security of a computer network, the method comprising:
identifying one or more attempted accesses from computing devices of the computer network to respective Internet-resource identifiers in an external network,
each of the Internet-resource identifiers having a respective Internet-resource-identifier rating that reflects a likelihood that one of a plurality of the Internet-resource identifiers is malicious, and
each of the computing devices having a respective device rating that reflects a likelihood that the computing device is infected by malware;
updating, based on the Internet-resource-identifier rating, the device rating of a respective one of the computing devices when the respective one of the computing devices attempts to access one of the plurality of Internet resources;
updating, based on the device rating, the Internet-resource-identifier rating of a respective one of the Internet resource identifiers when a respective one the computing devices attempts to access the respective one of the Internet resource identifiers, wherein the Internet-resource identifier rating of the respective one of the Internet resource identifiers is not assigned if the respective Internet-resource identifier is known to be non-malicious;
updating one or more of the device ratings in response to one or more failed Domain Name System (DNS) queries, based on at least one of the following; (i) a number of the failed DNS queries, (ii) a frequency of the failed DNS queries, or (iii) both the number and the frequency of the failed DNS queries, originating from the computing devices to which the one or more device ratings, respectively, belong; and
in response to at least one of the device ratings and Internet-resource-identifier ratings, ascertaining that the security of the computer network has been compromised, and generating an output in response thereto.
|