| CPC H04L 63/1425 (2013.01) [G06F 16/2228 (2019.01); G06F 16/2379 (2019.01); H04L 63/0209 (2013.01); H04L 63/1416 (2013.01); H04L 63/1433 (2013.01); H04L 63/1441 (2013.01); H04L 63/20 (2013.01); H04L 67/52 (2022.05)] | 20 Claims |
|
1. A method, comprising:
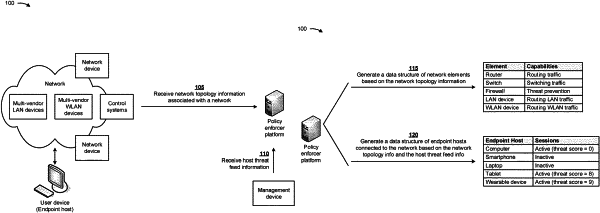
generating, by a device, a data structure of endpoint hosts that are each connected to a network and at least one network segment, of a plurality of network segments, of the network;
updating, by the device, the data structure based on a change in a state of a session associated with at least one endpoint host, of the endpoint hosts;
identifying, by the device and based on the data structure, a particular endpoint host, of the endpoint hosts, that changed location within the at least one network segment;
automatically determining, by the device, an action to enforce for the particular endpoint host that is triggered by the changed location within the at least one network segment;
identifying, by the device, a network control system that controls the at least one network segment associated with the particular endpoint host; and
causing, by the device, the action to be enforced, by the network control system, for the particular endpoint host.
|