| CPC H04L 63/1416 (2013.01) [H04L 12/1403 (2013.01); H04L 63/0442 (2013.01); H04L 63/1433 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
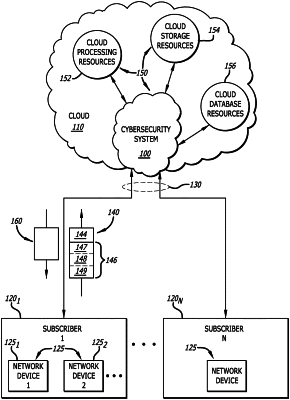
1. A cybersecurity system, including a processor and a non-transitory storage medium, for conducting cyberthreat analytics on a submitted object to determine whether the object is malicious, comprising:
a key management module stored within the non-transitory storage medium, the key management module, upon execution by the processor, assigns a first key to a subscriber upon registration and generates one or more virtual keys, based at least in part on the first key, for distribution to the subscriber, wherein a virtual key of the one or more virtual keys is included as part of a submission received from the subscriber to authenticate the subscriber to verify that the subscriber is authorized to perform one or more tasks associated with the submission, and each of the one or more virtual keys including the virtual key is set with a usage restriction that permits use of the virtual key when provided from a network device having a network address residing within a selected network address range; and
a consumption quota monitoring module stored within the non-transitory storage medium, the consumption quota monitoring module, upon execution by the processor, monitors a number of submissions received from the subscriber.
|