| CPC H04L 63/1416 (2013.01) [H04J 3/0667 (2013.01); H04L 61/4511 (2022.05); H04L 61/5007 (2022.05); H04L 63/029 (2013.01); H04L 63/0236 (2013.01); H04L 63/0245 (2013.01); H04L 63/1425 (2013.01); H04L 63/1466 (2013.01); H04L 63/1475 (2013.01)] | 20 Claims |
|
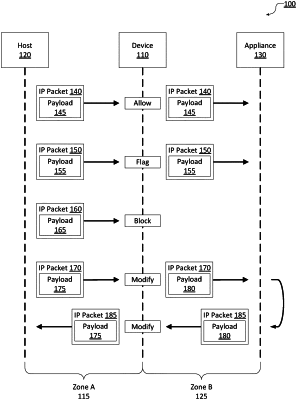
1. A method of preventing data exfiltration from a secure network, comprising:
receiving, at a device of a first network zone, a first internet protocol (IP) packet;
determining, by a processor of the device, that a first protocol above a network layer and a first size of the first IP packet matches a predetermined policy of a plurality of predetermined policies;
inspecting, by the processor, a first payload of the first IP packet based on the predetermined policy to identify a first format of the first IP packet;
detecting, by the processor responsive to inspecting the first payload, that the first payload includes a first set of data that violates the first format;
determining, by the processor responsive to detecting the first set of data, that the first IP packet improperly complies with the first format;
responsive to determining that the first IP packet improperly complies with the first format, truncating, by the processor, the first payload of the first IP packet to a size determined based on the first format, wherein truncating the first payload of the first IP packet includes removing the first set of data from the first payload;
receiving, at the device of the first network zone, a second IP packet;
determining, by the processor, that a second protocol above the network layer and a second size of the second IP packet matches the predetermined policy;
inspecting, by the processor, a second payload of the second IP packet based on the predetermined policy to identify a second source, a second destination, and a second format of the second IP packet;
determining, by the processor, that each of the second source, the second destination, and the second format is proper based on the predetermined policy; and
transmitting, by the processor, the second IP packet responsive to determining that the second format is proper.
|