| CPC H04L 63/04 (2013.01) [G06F 21/566 (2013.01); G06F 21/577 (2013.01); H04L 63/102 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/205 (2013.01); H04L 67/306 (2013.01); G06F 2221/034 (2013.01)] | 14 Claims |
|
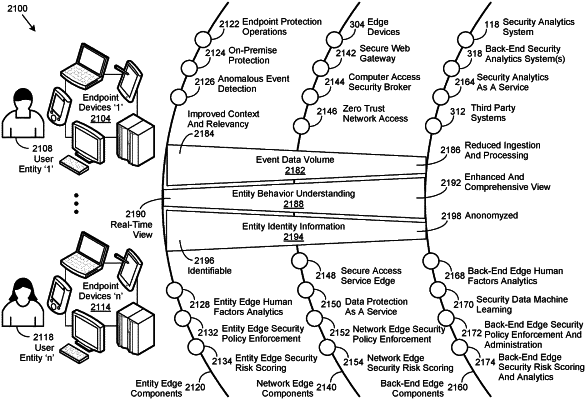
1. A computer-implementable method for performing a security operation, comprising:
monitoring a plurality of actions of an entity, the plurality of actions of the entity corresponding to a plurality of events enacted by the entity;
maintaining information relating to the monitoring within a user edge component;
identifying an event of analytic utility;
analyzing the event of analytic utility at the user edge component, the analyzing generating a security risk assessment, the analyzing being performed by a hardware processor of the user edge component;
providing the security risk assessment to a network edge component;
anonymizing the information relating to the monitoring to provide anonymized information; and,
providing the anonymized information to the network edge component; and wherein
the network edge component performs a security operation using the anonymized information relating to the monitoring; and,
the network edge component requests de-anonymized information from the user edge component when the security operation generates an indication of a security risk of the entity.
|