| CPC H04L 63/0884 (2013.01) [H04L 63/0281 (2013.01); H04L 63/20 (2013.01)] | 21 Claims |
|
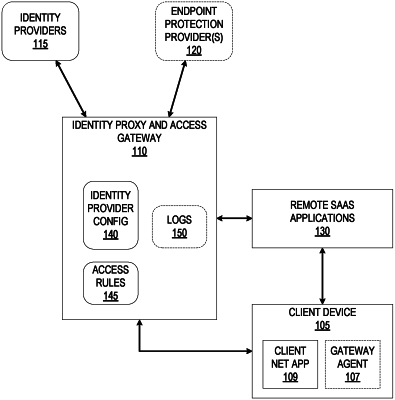
1. A method implemented in an identity proxy and access gateway, comprising:
receiving a first authentication request from a client device that has been generated by a third-party application in response to a first access request from the client device to the third-party application requesting access to a resource at the third-party application, wherein the first authentication request is requesting an authentication of a user that is attempting to access the third-party application, and wherein the identity proxy and access gateway is configured as a first identity provider of the third-party application;
transmitting an identity provider selection page to the client device, the identity provider selection page including one or more identity provider options for the user to select for authentication;
receiving, from the client device, a selection of one of the one or more identity provider options; causing the client device to transmit a second authentication request to a second identity provider corresponding to the selected one of the one or more identity provider options;
receiving, from the client device, a first authentication response that was generated by the second identity provider that indicates the user has successfully authenticated to the second identity provider;
enforcing a first set of one or more access rules to determine whether the user is permitted to access the third-party application, wherein the first set of one or more access rules is enforced independently from any rules enforced at the second identity provider;
determining, from the enforcing of the first set of one or more access rules, that the user is permitted to access the third-party application, and responsive to this determination, generating a second authentication response that-indicates the user has successfully authenticated; and
transmitting the second authentication response to the client device, wherein the second authentication response is caused to be transmitted to the third-party application that indicates the user has successfully authenticated.
|