| CPC H04L 63/061 (2013.01) [H04L 9/3247 (2013.01); H04L 63/0435 (2013.01); H04L 63/166 (2013.01)] | 20 Claims |
|
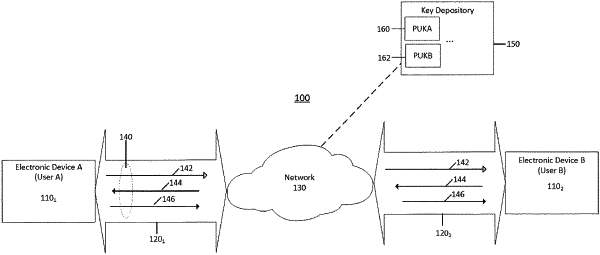
1. A computer-implemented method comprising, as performed by a first computing device associated with a sender of transmissions:
generating first encrypted data using first data and a public key assigned to an intended recipient;
sending, to a second computing device, a first transmission comprising the first encrypted data;
receiving, from the second computing device, a second transmission comprising (1) a first digital signature signed by a private key assigned to the intended recipient and (2) second encrypted data encrypted using a public key assigned to the sender, wherein the second encrypted data comprises an encrypted version of the first data and second data, and wherein the first digital signature comprises a representation of the first data and the second data;
recovering the first data and the second data from the second transmission using a private key assigned to the sender; verifying that the second transmission originated from the intended recipient based at least partly on the first digital signature;
generating third encrypted data using at least a portion of the second data and the public key assigned to the intended recipient;
generating a second digital signature singed by the private key assigned to the sender, wherein the second digital signature comprises a representation of at least the portion of the second data; and
sending, to the second computing device, a third transmission comprising the second digital signature and the third encrypted data, wherein the second digital signature is provided to verify non-tampering of the second data during transit from the second computing device of the first computing device.
|