| CPC H04L 63/0263 (2013.01) [H04L 63/14 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
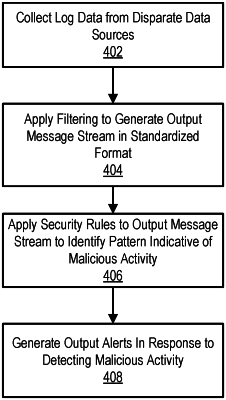
1. A method of generating security alerts comprising:
obtaining an input message stream from a set of data sources, wherein the input message stream comprises a sequence of input security-related data entries in different respective native formats that varies between different data sources of the set of data sources;
identifying a data format of a current input message of the input message stream using a set of detection rules, the current input message received from a current data source;
parsing the current input message, based on the identified data format of the current input message, to generate parsed message content, wherein the parsing comprises separating the current input message into key-value pairs;
applying a set of filter selection rules to the parsed message content to identify a filter from the set of filters for use with messages received from the current data source, wherein the filter selection rules identify a pattern associated with the current data source to identify the filter from the set of filters, and wherein each filter of the set of filters corresponds with one of the native formats of the different data sources of the set of data sources;
applying, by a processor, the identified filter to the parsed message content to transform the parsed message content to a current output message of an output message stream, wherein each output message of the output message stream comprises output security-related data entries in a standardized format independent of the data source;
applying a set of security rules to the output message stream to detect a data pattern indicative of malicious activity; and
generating a security alert to an administrative interface indicative of the detected data pattern.
|