| CPC H04L 47/783 (2013.01) [H04L 47/765 (2013.01); H04L 47/821 (2013.01); H04L 47/828 (2013.01); H04L 63/12 (2013.01)] | 20 Claims |
|
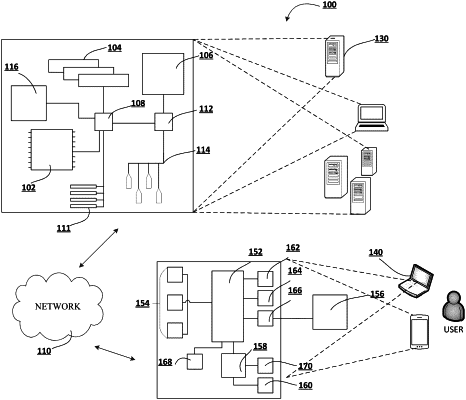
1. A system for executing digital resource transfer using trusted computing, the system comprising:
at least one processor; and
at least one memory operatively coupled to the at least one processor, the at least one memory containing instructions that, when executed by the at least one processor, cause the at least one processor to:
receive, from a second computing device, an indication that a first computing device has initiated a transfer of a digital resource;
initiate, via the second computing device, an authentication protocol on the first computing device and the digital resource in response to receiving the indication;
trigger, using the authentication protocol, a mutual authentication between the first computing device and the second computing device based on at least, (i) the first computing device and the second computing device are running a trusted computing environment, (ii) an authentication information type associated with the first computing environment and the second computing environment, and (iii) a syntax associated with the mutual authentication;
in an instance in which the first computing device and the second computing device are mutually authenticated, determine, using the authentication protocol, that the first computing device is in secure possession of the digital resource, wherein determining further comprises:
retrieve information associated with one or more data repositories used to store the digital resource;
determining that the one or more data repositories operate within one or more secure rails based on at least the information associated with the one or more data repositories indicating that the one or more data repositories are not compromised; and
determining a nonce associated with the digital resource, wherein the nonce indicates a number of times the digital resource has been transferred from one computing device to another, and wherein the nonce meets a security requirement;
initiate, via the second computing device, a request to receive the digital resource from the first computing device based on at least determining that the first computing device is in secure possession of the digital resource;
receive, via the second computing device, an indication that the second computing device has received the digital resource from the first computing device;
initiate, via the second computing device, a resource verification protocol on the digital resource;
verify, using the resource verification protocol, one or more digital signatures associated with the digital resource, wherein verifying further comprises determining that the digital resource has been authenticated by an issuing entity by a public digital signature, wherein the public digital signature associated with the issuing entity is recorded in a first encryption layer associated with the digital resource; and
transmit, via the second computing device, an acknowledgement to the first computing device that the one or more digital signatures associated with the digital resource has been verified.
|