| CPC H04L 63/20 (2013.01) [G06F 16/2246 (2019.01); H04L 43/08 (2013.01); G06F 9/45558 (2013.01); G06F 2009/45562 (2013.01); G06F 2009/45595 (2013.01)] | 20 Claims |
|
1. A system comprising:
one or more processors; and
at least one non-transitory computer-readable storage medium having stored therein instructions which, when executed by the one or more processors, cause the system to:
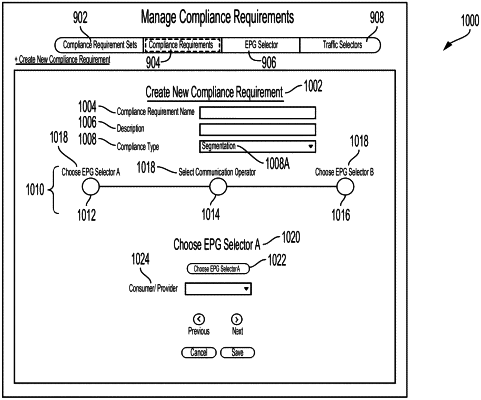
create a security compliance requirement for a network, the security compliance requirement comprising group selectors, a traffic selector, and a communication operator, wherein the group selectors represent sets of groups, wherein the traffic selector identifies traffic matching one or more traffic parameters, and wherein the communication operator defines a condition for traffic corresponding to the group selectors and the traffic selector;
determine that respective groups in one or more pairs of endpoint groups from the sets of groups are associated with respective different network contexts, wherein the respective different network contexts comprise one or more of a private network context, a network domain contact, a virtual routing and forwarding instance context, a subnet context and a bridge domain context;
for each pair of the endpoint groups, create a first respective data structure representing the pair of endpoint groups, the communication operator, and the traffic selector;
create a second respective data structure representing a first portion of a logical model of the network, the first portion of the logical model representing a subset of the logical model of the network and containing policies corresponding to one context of the respective different network contexts;
determine whether the first respective data structure is contained in the second respective data structure to yield a containment check; and
determine, in response to the containment check, whether policies for traffic between respective groups in the one or more pairs of endpoint groups comply with the security compliance requirement.
|