| CPC G06Q 20/023 (2013.01) [G06Q 20/0425 (2013.01); G06Q 20/401 (2013.01); G06Q 40/02 (2013.01)] | 24 Claims |
|
15. A method of facilitating secured user changes to future recurring transfers associated with a user having an employer associated with an external institution, the method, comprising:
receiving, by a permissions management system, a request to change future recurring transfers,
wherein the permissions management system comprises one or more processors;
receiving, by the permissions management system, an identification of the user;
identifying, by the permissions management system, an employer associated with the identified user;
identifying, by the permissions management system, an external institution associated with the future recurring transfers, from a database that matches employers to external institutions based on the identified employer;
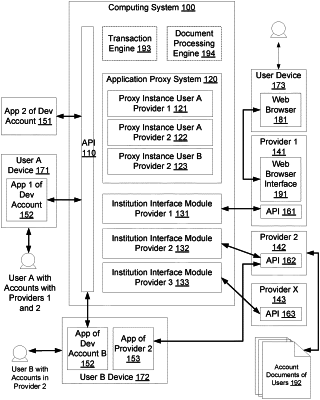
initiating, by the permissions management system and based on the identified external institution, a simulated instance of a software application of the external institution to determine a set of endpoints and a set of the future recurring transfers to endpoints, of the set of endpoints, associated with the identified user, wherein the simulated instance of the software application is configured to appear as a first-party application installed on a user device from the perspective of the external institution, and wherein the simulated instance is specifically configured to interface with an application programming interface (“API”) of the external institution with computing devices associated with the external institution;
receiving, by the permissions management system, a request from the user to change at least one of the set of the endpoints and the set of the future recurring transfers to the endpoints; and
executing, by the permissions management system and based on, using the simulated instance, executing the requested change to at least one of the set of the endpoints or the set of the future recurring transfers to the endpoints.
|