| CPC G06F 21/577 (2013.01) [G06F 21/552 (2013.01); G06F 21/566 (2013.01)] | 17 Claims |
|
1. A computer-implemented method for identifying a security vulnerability in an application executing on a host computing device in a distributed computing environment, comprising:
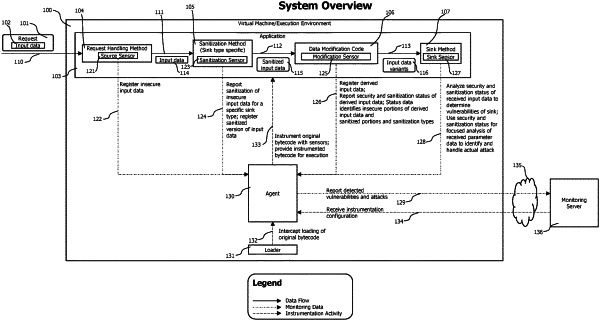
registering, by a source sensor, input data in a security status repository on the host computing device, where the input data is received from a source external to the host computing device and the source sensor is instrumented in a request handling method of the application;
logging, by a sanitization sensor, sanitization of the input data in the security status repository, where the logging of the sanitization is in response to execution of a data sanitization method within the application and the sanitization sensor is instrumented in the data sanitization method;
logging, by a sink sensor, a sink call made by the application in the security status repository, where the logging of the sink call is in response to execution of the sink call and the execution of the sink call uses at least a portion of the input data;
determining, by an agent, whether parameter values for the sink call were sanitized using data in the security status repository, where a portion of the parameter values for the sink call are from the input data and the agent is deployed in an execution environment shared with the application; and
identifying, by the agent, a security vulnerability in the application in response to a determination that at least a portion of one parameter value for the sink call was not sanitized.
|