| CPC G06F 21/53 (2013.01) [G06F 12/1408 (2013.01); G06F 21/6218 (2013.01); H04L 9/0822 (2013.01); G06F 2212/1052 (2013.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
1. A method comprising:
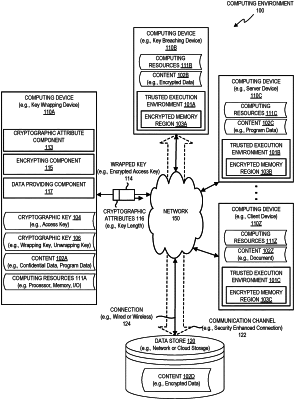
accessing, by a processing device, a wrapped key that encodes a cryptographic key;
executing, by the processing device in a trusted execution environment, instructions to derive the cryptographic key in view of the wrapped key, wherein the executing to derive the cryptographic key comprises a task that consumes computing resources for a duration of time;
using the cryptographic key to access program data;
executing, by the processing device, the program data, wherein the executed program data evaluates a condition related to the duration of time; and
transmitting a message comprising an indication of the evaluated condition, wherein the message indicates that the cryptographic key has been derived in view of the wrapped key within a predetermined minimum threshold time.
|