| CPC G06F 11/1464 (2013.01) [G06F 11/1461 (2013.01); G06F 11/1469 (2013.01); H04L 9/0863 (2013.01); H04L 9/0894 (2013.01)] | 15 Claims |
|
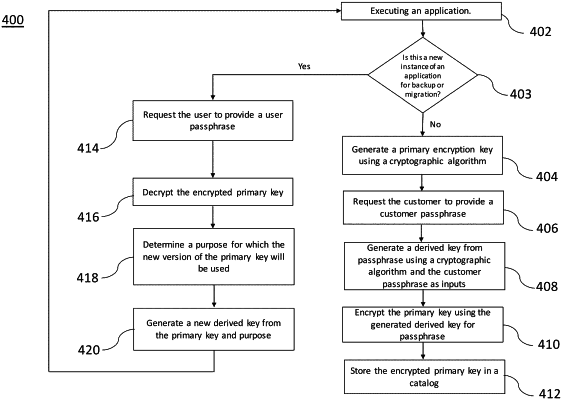
1. A computer-implemented method, comprising:
executing an initial non-backup instance of an application;
generating a primary key using a cryptographic algorithm;
receiving a passphrase configured to encrypt and decrypt the primary key;
generating a derived key from the passphrase using the cryptographic algorithm;
encrypting the primary key using the derived key, thereby producing an encrypted primary key;
storing the encrypted primary key in a catalog;
executing a first instance of the application for backup;
decrypting the encrypted primary key in the catalog, thereby retrieving the primary key;
determining that the primary key is to be used for a first purpose of a backup repository end point for the first instance of the application; and
generating a derived key for the first instance of the application based on the primary key and the first purpose, wherein the derived key for the first instance of the application is distinct from a derived key for a second instance of the application, wherein the derived key for the second instance of the application is to be used for a second purpose of a policy for an operation for the second instance of the application.
|