| CPC H04L 9/3213 (2013.01) [G06F 3/067 (2013.01); G06F 3/0622 (2013.01); G06F 3/0659 (2013.01); G06F 16/245 (2019.01); G06F 21/6218 (2013.01); G06F 21/6254 (2013.01); H04L 9/0869 (2013.01); H04L 9/0894 (2013.01); H04L 63/0853 (2013.01); H04L 63/102 (2013.01); H04L 2209/08 (2013.01)] | 20 Claims |
|
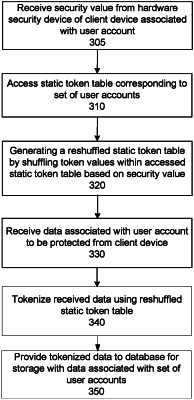
1. A method for securing data in a centralized environment comprising:
in response to receiving a request to protect data from the client device, providing, by the central server, an encrypted security value previously encrypted and provided by the client device and stored by the central server before receiving the request to protect data from the client device to the client device for decryption and receiving a decrypted security value from the client device in response;
accessing, by the central server, a token table mapping each of a plurality of input values to a different token value;
tokenizing, by the central server, the data using the token table by querying the token table with a value of a portion of the data to identify a token value mapped to the value of the portion of the data and replacing the portion of the data with the identified token value; and
providing, by the server, the tokenized data to a database for storage in conjunction with tokenized data corresponding to other user accounts such that an unauthorized access to tokenized data corresponding to a first user account does not compromise tokenized data corresponding to a second user account.
|