| CPC H04L 9/088 (2013.01) | 18 Claims |
|
1. A proving computing system comprising:
a host processor that executes a software program; and a cryptographic processor that integrates a witness generator, a proof generator and a local witness buffer, wherein the local witness buffer integrated with the witness generator and the proof generator on the cryptographic processor is separate from host memory accessed by the host processor;
wherein the cryptographic processor including the witness generator, the proof generator and the local witness buffer is implemented as a semiconductor device separate from the host processor;
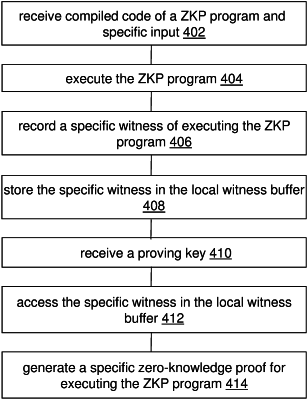
wherein the witness generator on the cryptographic processor (a) receives, from the software program running on the host processor, compiled code of a zero-knowledge-proof (ZKP) program and specific input to the ZKP program, (b) executes the ZKP program by way of executing the compiled code, (c) records specific output generated from the ZKP program with the specific input, intermediate variable values, and the specific input, as a specific witness of executing the ZKP program, and (d) stores the specific witness in the local witness buffer;
wherein the specific witness has a data size exceeding a maximum supported memory access bandwidth of the host memory for a single clock cycle;
wherein the proof generator on the cryptographic processor (e) receives, from the software program running on the host processor, a proving key that was generated along with a verification key, (f) accesses the specific witness in the local witness buffer, wherein the specific witness is accessed in its entirety by the proof generator over a first total number of clock cycles fewer than a second total number of clock cycles over which host memory stored data of the same data size is accessed from the host memory and (g) generates a specific zero-knowledge proof for executing the ZKP program with a combination of the proving key, the specific witness and the specific input;
wherein a recipient computing system that receives the verification key and the specific zero-knowledge proof validates the specific zero-knowledge proof with the verification key.
|