| CPC H04L 9/088 (2013.01) [G06F 21/64 (2013.01); H04L 9/3236 (2013.01)] | 16 Claims |
|
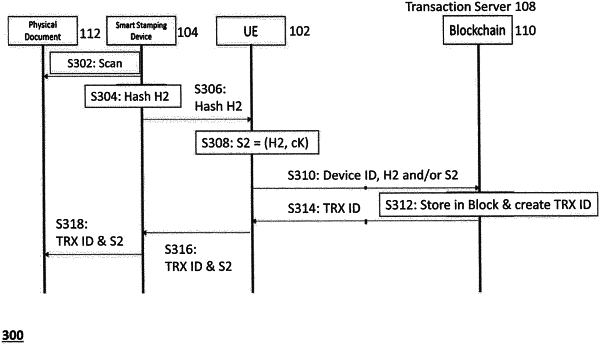
1. A device for controlling cryptographic document protection, the device being associated with a device identifier (Device ID) and with a cryptographic key (cK), wherein the device is configured to:
obtain an electronically processable document representation, EPDR, (H2), of content of a document that is to be protected;
apply the cryptographic key (cK) to the EPDR (H2) to obtain a cryptographically processed document representation, CPDR, (S2);
transmit the device identifier (Device ID) and a verification parameter comprising at least one of the EPDR (H2) and the CPDR (S2) towards a transaction server that is configured to log the device identifier (Device ID) and the verification parameter (S2, H2) in a tamper-proof manner;
receive a transaction identifier (TRX ID) associated with the device identifier (Device ID) and the verification parameter (S2, H2); and
trigger printing of the transaction identifier (TRX ID) and the CPDR (S2) on a physical document that corresponds to the EPDR (H2).
|