| CPC H04L 63/1433 (2013.01) [G06F 8/65 (2013.01); H04L 63/1441 (2013.01); H04L 67/75 (2022.05)] | 20 Claims |
|
1. A method, performed by one or more processors, the method comprising:
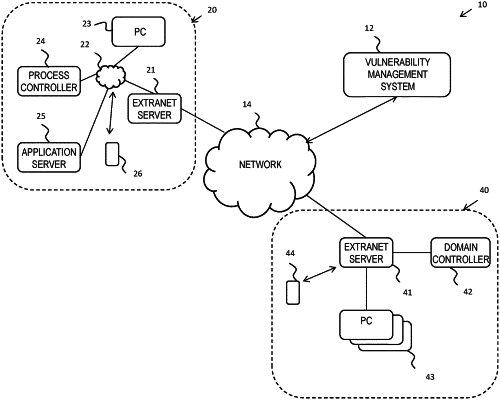
receiving first data representing an infrastructure of a computer network, the first data comprising an indication of a plurality of hosts which form at least part of the computer network and one or more software resources on respective hosts;
receiving second data from a vulnerability scanning software, the second data comprising an indication of one or more vulnerabilities detected in the one or more software resources provided on at least some of the plurality of hosts of the computer network;
generating, using a combination of the first data and the second data, output data representing a risk profile of the computer network infrastructure; and
determining a patch deployment strategy based on one or more prioritization rules and the output data, the one or more prioritization rules determining an order of one or more patches to deploy to remedy the detected vulnerabilities, wherein the deployment strategy determines a least number of patches required to remedy the detected vulnerabilities.
|