| CPC H04L 63/1416 (2013.01) [H04L 63/0876 (2013.01); H04L 63/102 (2013.01); H04L 63/1441 (2013.01); H04L 63/20 (2013.01)] | 16 Claims |
|
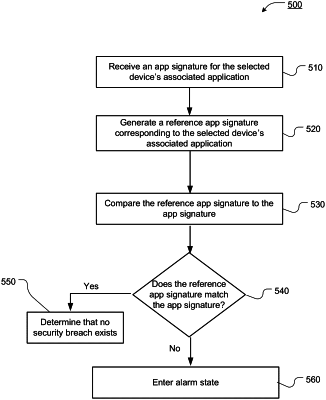
1. A computer-implemented method of monitoring security of a set of computing devices in a distributed system, the distributed system having a plurality of computing devices, each computing device executing an application associated with said device, the computing devices being in communication with one another over a network, the security being monitored by a security program causing execution of security computer processes in a computer node, the security computer processes comprising:
generating, by a selected device in the set of computing devices, by applying a set of computer processes G( ) to the selected device's associated application, an app signature for the selected device's associated application;
receiving, by the computer node, from the selected device, the app signature for the selected device's associated application;
generating, by the computer node a reference app signature for a reference application, in an application repository, corresponding to the selected device's associated application, wherein the reference application is another instance of the selected device's associated application, and has been generated by the computer node from a functional replica of the associated application stored in the application repository through a set of computer processes F( );
comparing, by the computer node, the reference app signature to the app signature of the associated application of the selected device;
determining, by the computer node, a potential security breach if the reference app signature fails to match the app signature of the associated application of the selected device; and
if the reference app signature does fail to match the app signature of the associated application of the selected device, then causing the computer node to enter an alarm state.
|