| CPC H04L 63/1416 (2013.01) [G06N 5/025 (2013.01); G06N 20/00 (2019.01)] | 29 Claims |
|
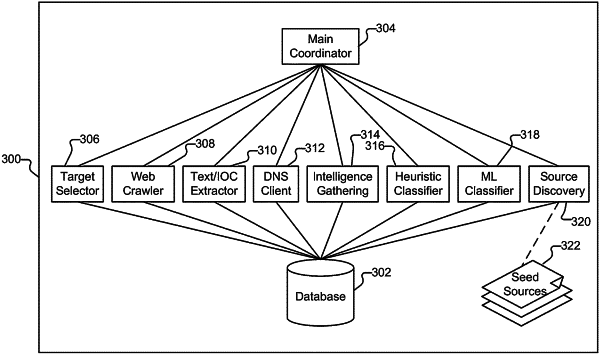
1. A system, comprising:
a processor configured to:
receive a set of potential sources for Indicators of Compromise (IOCs);
extract one or more candidate IOCs from at least one source included in the set of potential sources, including by determining that a URL was defanged;
automatically identify an actionable IOC from the one or more candidate IOCs; and
provide the actionable IOC to a security enforcement service, including by reverse defanging the URL; and
a memory coupled to the processor and configured to provide the processor with instructions.
|