| CPC H04L 45/122 (2013.01) [H04L 45/02 (2013.01); H04L 45/20 (2013.01)] | 20 Claims |
|
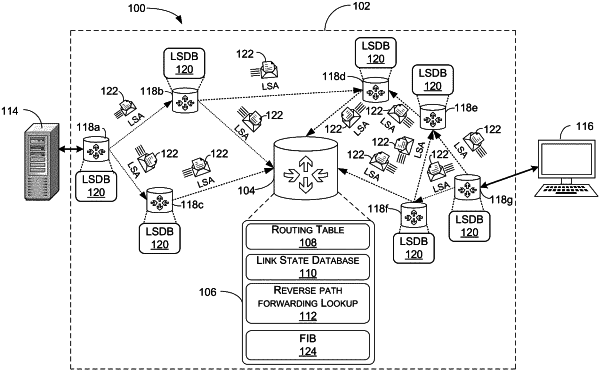
1. A method performed by a network switching device connected with a computer network, the method comprising:
receiving by the network switching device, network topology information from a node of the network;
updating a link-state database of the network switching device based on the network topology information;
receiving a data packet associated with a data flow between one or more nodes of the computer network and the network switching device;
determining whether the data packet was received from a reverse path forwarding interface;
in response to determining that the data packet was received from a reverse path forwarding interface, sending the data packet from the network switching device to a next-hop node of the computer network;
in response to determining that the data packet was not received from a reverse path forwarding interface performing a shortest path first calculation rooted at a router advertising a source network of the data packet;
determining whether the data packet was received from a valid path of the computer network based on the shortest path first calculation;
in response to determining that the data packet was received from a valid path, sending the data packet from the network switching device to the next-hop node of the computer network; and
in response to determining that the data packet was not received from a valid path of the computer network, dropping the data packet.
|