| CPC G06F 9/3867 (2013.01) [G06F 9/30058 (2013.01)] | 20 Claims |
|
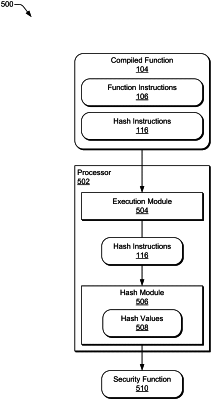
9. A method performed by a computing device, the method comprising:
executing function instructions to arrive at a target executed-instruction state, the function instructions:
comprised by a plurality of basic blocks of the function instructions;
having at least two execution paths between a first basic block and a second basic block of the plurality of basic blocks, and
the target executed-instruction state being within the second basic block;
executing hash instructions within the plurality of basic blocks to arrive at a hash value at the target executed-instruction state, the hash instructions including respective hash-input instructions within each of the plurality of basic blocks other than the second basic block;
comparing the hash value at the target executed-instruction state to an expected hash-value at the target executed-instruction state, the expected hash-value at the target executed-instruction state determined based on an initial hash-value, a canonical value, and a hash function, the expected hash-value at the target executed-instruction state irrespective of which of the execution paths were executed; and
responsive to the hash value at the target executed-instruction state not matching the expected hash-value of the executed-instruction state, performing a security function.
|