| CPC H04L 9/3247 (2013.01) [G06F 21/32 (2013.01); H04L 9/14 (2013.01)] | 26 Claims |
|
1. A method, comprising:
transmitting, from a client network application of a client device, a first request for a first network resource to a server;
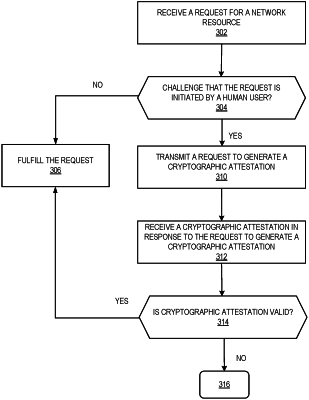
receiving, from the server, a second request to challenge that the first request was initiated by a human user through verifying a first physical interaction between the human user and a hardware component, the second request being received prior to the first network resource being received at the client network application;
causing a first prompt to be displayed to perform the first physical interaction with the hardware component;
receiving a first cryptographic attestation that includes a first attestation signature that is generated after confirmation that the first physical interaction was performed with the hardware component;
generating a first zero-knowledge proof of the first attestation signature at the client device;
transmitting, from the client network application to the server, the first zero-knowledge proof of the first attestation signature for verification;
receiving the first network resource responsive to the server verifying the validity of the first zero-knowledge proof of the first attestation signature;
transmitting, from the client network application of the client device, a third request for a second network resource to the server;
receiving, from the server, a fourth request to challenge that the third request was initiated by a human user through verifying a second physical interaction between the human user and the hardware component, the third request being received prior to the second network resource being received at the client network application;
causing a second prompt to be displayed to perform the second physical interaction with the hardware component;
receiving a second cryptographic attestation that includes a second attestation signature that is generated after confirmation that the second physical interaction was performed with the hardware component;
generating a second zero-knowledge proof of the second attestation signature at the client device;
transmitting, from the client network application to the server, the second zero-knowledge proof of the second attestation signature for verification;
receiving a request for the human user to participate in a CAPTCHA challenge responsive to the server determining that the second zero-knowledge proof cannot be verified as valid;
presenting the CAPTCHA challenge;
transmitting, from the client network application to the server, a response to the CAPTCHA challenge; and
receiving the second network resource responsive to the server verifying the response to the CAPTCHA challenge.
|