| CPC H04L 9/0872 (2013.01) [G06F 16/9537 (2019.01); H04L 9/08 (2013.01); H04L 9/0819 (2013.01); H04L 9/088 (2013.01); H04L 63/0428 (2013.01); H04L 63/0876 (2013.01); H04W 12/033 (2021.01); H04W 12/041 (2021.01); H04W 12/06 (2013.01); H04L 2209/601 (2013.01); H04L 2209/80 (2013.01); H04N 21/25816 (2013.01); H04N 21/4821 (2013.01); H04N 21/63345 (2013.01)] | 18 Claims |
|
1. A device, comprising:
a processing system including a processor; and
a memory that stores executable instructions that, when executed by the processing system, facilitate performance of operations, the operations comprising:
authenticating a communication device based on communication over a first plane of a network, wherein the authenticating comprises:
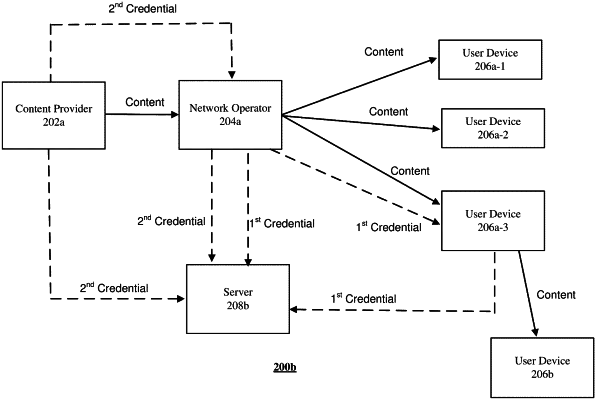
performing a first comparison of a first instance of a first credential received from the communication device as part of the communication over the first plane of the network with a second instance of the first credential received from a network operator of the network, wherein the communication device receives the first credential from the network operator, and wherein the first credential is not associated with any content provider;
determining that a match exists between the first instance of the first credential and the second instance of the first credential based on the first comparison;
performing a second comparison of a first instance of a second credential received from the network operator of the network with a second instance of the second credential received from a content provider; and
determining that a match exists between the first instance of the second credential and the second instance of the second credential based on the second comparison;
responsive to the authenticating, determining a location of the communication device resulting in a determined location;
responsive to the authenticating, generating a first decryption key that is based on the determined location of the communication device;
transmitting the first decryption key to the communication device;
transmitting encrypted content associated with the content provider to the communication device over a second plane of the network, wherein a first portion of the encrypted content is accessible at the communication device via the first decryption key, and wherein the first decryption key is based on a constraint that limits accessibility to the first portion of the encrypted content via the first decryption key to a distance that is within a threshold of the determined location of the communication device;
receiving a request for a second decryption key from the communication device following an expiration of a timeout measured relative to when the first decryption key is transmitted; and
based on the receiving of the request for the second decryption key, transmitting the second decryption key to the communication device.
|