| CPC H04L 63/20 (2013.01) [H04L 63/0876 (2013.01); H04L 63/104 (2013.01)] | 20 Claims |
|
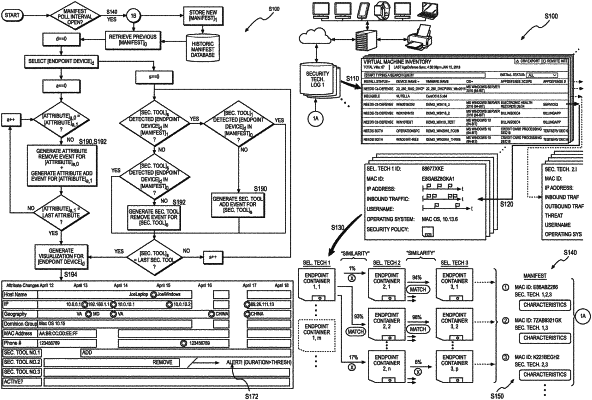
1. A method comprising:
populating a device record with a first set of characteristics representing a first endpoint device in a set of endpoint devices, the first set of characteristics:
generated by a set of security technologies during a first time interval; and
representing:
detection of the first endpoint device by a first security technology in a set of security technologies during the first time interval; and
detection of the first endpoint device by a second security technology in the set of security technologies during the first time interval;
populating the device record with a second set of characteristics representing the first endpoint device, the second set of characteristics:
generated by the set of security technologies; and
representing detection of the first endpoint device by the first security technology during a second time interval;
in response to absence of detection of the first endpoint device by the second security technology during the second time interval, generating a first source remove event specifying removal of the second security technology from the first endpoint device; and
in response to a third set of characteristics identifying the first endpoint device, labeling the first endpoint device as active in an endpoint device inventory list associated with a computer network during a third time interval.
|