| CPC H04L 63/12 (2013.01) [G06F 16/27 (2019.01); G06F 21/44 (2013.01); G06F 21/64 (2013.01); H04L 9/0643 (2013.01); H04L 9/3236 (2013.01); H04L 61/4511 (2022.05); H04L 63/126 (2013.01); H04L 63/1466 (2013.01); H04L 67/568 (2022.05); G06F 16/2379 (2019.01); H04L 9/50 (2022.05)] | 14 Claims |
|
1. A method, comprising:
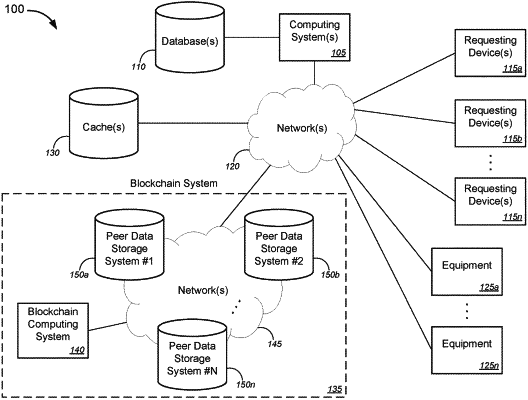
receiving, with a computing system and from a requesting device, a first request for first data that is output by first equipment;
in response to receiving the first request for the first data, retrieving, with the computing system, the first data that is output by the first equipment;
analyzing, with the computing system, the first data to determine whether the first data as output by the first equipment can be trusted;
based on a determination that the first data as output by the first equipment is deemed to be trusted data, sending, with the computing system, the first data to the requesting device;
based on a determination that the first data is deemed to require further data validation, sending, with the computing system and to a blockchain system, a second request for identifying a blockchain containing a block containing a copy of the first data that is output by the first equipment; and
in response to the blockchain system identifying the blockchain containing a copy of the first data that is output by the first equipment, performing the following:
receiving, with the computing system, a copy of the identified blockchain from the blockchain system;
abstracting, with the computing system and from the identified blockchain, the block containing the copy of the first data;
abstracting, with the computing system and from the block, the copy of the first data that is output by the first equipment; and
sending, with the computing system, the first data to the requesting device,
wherein the first data comprises at least one or more portions of a log of interactions between a user and a service provider, and
wherein the interactions between the user and the service provider comprises at least software application usage.
|