| CPC G06F 21/316 (2013.01) [G06F 21/32 (2013.01); G06N 3/045 (2023.01); G06N 3/0464 (2023.01); G06N 3/082 (2013.01)] | 20 Claims |
|
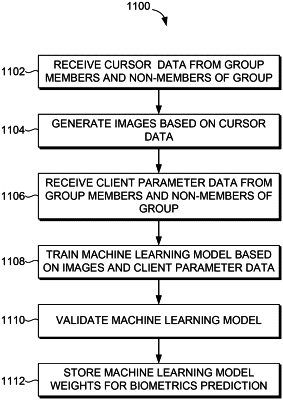
1. A computer-implemented method, comprising:
receiving first cursor movement data representing one or more cursor movements captured via a client device, wherein the first cursor movement data comprises coordinates of a cursor during the one or more cursor movements and at least one of a speed of the cursor or a direction of the cursor at each of the coordinates;
generating a visual depiction of the coordinates of the cursor, including a plurality of image parameters, the plurality of image parameters comprising at least a first image parameter that encodes the speed of the cursor, and a second image parameter that encodes the direction of the cursor;
receiving a first set of client parameters that are associated with the client device;
analyzing the visual depiction and the first set of client parameters using a machine learning model to generate a prediction result, wherein the machine learning model is trained based on second cursor movement data and a second set of client parameters associated with a first group of client devices to identify fraudulent activity; and
generating, based on the prediction result, an output indicating whether the client device is associated with particular activity identified by the second cursor movement data and a second set of client parameters as fraudulent.
|