| CPC H04W 12/06 (2013.01) [G06F 3/041 (2013.01); G06F 21/31 (2013.01); G06F 21/316 (2013.01); G06F 21/554 (2013.01); G06F 21/83 (2013.01); H04L 63/0861 (2013.01); H04M 1/72403 (2021.01); G06F 21/32 (2013.01)] | 17 Claims |
|
1. A system comprising:
one or more processors, that are configured to execute code;
wherein the one or more processors are operably associated with one or more memory units that are configured to store code;
wherein the one or more processors are configured to perform a process comprising:
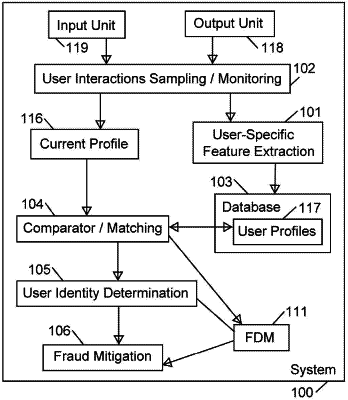
(a) monitoring input-unit interactions of a user, who utilizes during a usage session one or more input units of an electronic device to fill-out data in a fillable form of a computerized service;
(b1) if said input-unit interactions indicate that said user utilized keyboard shortcuts for data entry or for navigation, then increasing an attack-relatedness score of said usage session;
(b2) detecting a particular average typing speed of said user in said usage session; and if said particular average typing speed matches one or more average typing speeds that are pre-defined as average typing speeds of attackers, then increasing said attack-relatedness score of said usage session;
(c) if said attack-relatedness score of said usage session is greater than a particular threshold value, then: determining that said input-unit interactions are part of an attack, and initiating one or more mitigation operations;
wherein the process further comprises:
defining a first field in said fillable form, as a field that users are familiar with and type data therein at a typing speed that is greater than a pre-defined value;
defining a second field in said fillable form, as a field that users are unfamiliar with and type data therein at a typing speed that is smaller than or equal to said pre-defined value;
detecting that a rate of manual data entry by said user into the first field, is generally similar to a rate of manual data entry by said user into the second field;
based on said detecting of the rate of manual data entry, determining that said user is an attacker posing as an authorized user and gaining unauthorized access to the computerized service.
|